RPKI инфраструктура: RIPE validator и RPKI-to-Router Protocol сервер для Juniper MX
13 Apr 2020 - slepwin
Share on:В статье описывается внедрение RPKI 1 инфраструктуры на примере двух RPKI Validator 2 и RTR Server 3 от RIPE NCC 4 и Cloudflare 5 , а также соответствующая конфигурация Junos OS для Juniper MX.
Сетевая топология
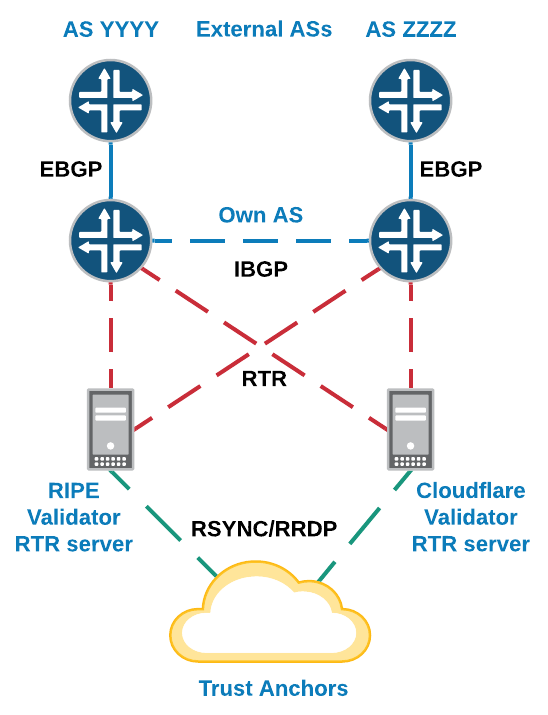
Установка и настройка RIPE Validator + RTR Server
- Установка из репозитория RIPE NCC 4 для дистрибутивов на базе RHEL 6:
sudo yum update # Adding RPM repo sudo yum-config-manager --add-repo https://ftp.ripe.net/tools/rpki/validator3/prod/centos7/ripencc-rpki-prod.repo # Install necessary packages sudo yum install yum-utils rpki-validator rpki-rtr-server # Enable services and run them sudo systemctl enable rpki-validator-3 rpki-rtr-server sudo systemctl start rpki-validator-3 rpki-rtr-server # Check both services are running sudo systemctl is-active rpki-validator-3 rpki-rtr-server - Базовая настройка конфигурации RPKI валидатора:
# Edit RPKI validator configuration sudo nano /etc/rpki-validator-3/application.properties server.address=0.0.0.0Базовая настройка конфигурации RTR сервера:
# Edit RTR server configuration sudo nano /etc/rpki-rtr-server/application.properties server.address=0.0.0.0 rtr.server.address=0.0.0.0 rtr.server.port=8323Примечание: Для безопасности необходимо указать IP-адреса интерфейсов, на которых будут работать сервисы, настроить фаервол, а также реверс-прокси для доступа по HTTP/HTTPS.
- Перезапуск сервисов:
# Restart both services sudo systemctl restart rpki-validator-3 rpki-rtr-server- RPKI Validator 3.1 должен быть доступен по http://x.x.x.x:8080/
- Проверить RPKI Validator API можно по http://x.x.x.x:8080/swagger-ui.html
- RTR Server должен быть доступен по tcp x.x.x.x:8323
- Установка ARIN TAL (остальные Trust Anchors встроены):
# Download file to temporary directory wget https://www.arin.net/resources/manage/rpki/arin-ripevalidator.tal -O /tmp/arin-ripevalidator.tal # Install ARIN TAL upload-tal.sh /tmp/arin-ripevalidator.tal http://localhost:8080/ # Remove previously downloaded file rm /tmp/arin-ripevalidator.tal - Проверка работоспособности сервисов:
# Check status for both services sudo systemctl status rpki-validator-3 rpki-rtr-server sudo ss -tulpn | egrep '8080|8323'
Установка и настройка Cloudflare OctoRPKI и GoRTR сервера
- Установка OctoRPKI 7 и GoRTR 8 для дистрибутивов на базе RHEL 6:
# Install curl and jq as they are support tools sudo yum update sudo yum install curl jq # Install latest RPM packages for OctoRPKI and GoRTR sudo yum install $(for repo in cfrpki gortr; do curl -s https://api.github.com/repos/cloudflare/$repo/releases | jq 'first(.[].assets[] | select(.name | contains("rpm"))) | .browser_download_url' -r; done)Где вложенная команда
for repo in cfrpki gortr; do curl -s https://api.github.com/repos/cloudflare/$repo/releases | jq 'first(.[].assets[] | select(.name | contains("rpm"))) | .browser_download_url' -r; doneВыбирает последние доступные версии RPM пакетов из релизов репозиториев OctoRPKI 7 и GoRTR 8.
-
Настройка обоих сервисов:
Создание файла сервиса systemd для OctoRPKI 7:
# Create OctoRPKI systemd service file sudo cat <<EOF > /etc/systemd/system/octorpki.service [Unit] Description=OctoRPKI After=network.target [Service] Type=simple EnvironmentFile=/etc/default/octorpki WorkingDirectory=/usr/share/octorpki ExecStart=/usr/bin/octorpki -mode server -output.sign.key /opt/cfrpki/keys/private.pem Restart=always RestartSec=60 StandardOutput=syslog StandardError=syslog SyslogIdentifier=cf-octorpki [Install] WantedBy=multi-user.target EOFСоздание файла сервиса systemd для GoRTR 8:
# Create GoRTR systemd service file sudo cat <<EOF > /etc/systemd/system/gortr.service [Unit] Description=GoRTR After=octorpki.service [Service] Type=simple EnvironmentFile=/etc/default/gortr WorkingDirectory=/usr/share/gortr ExecStartPre=/bin/sleep 30 ExecStart=/usr/bin/gortr -bind :8323 -verify.key /opt/cfrpki/keys/public.pem -cache http://localhost:8080/output.json -metrics.addr :8081 -refresh=120 Restart=always RestartSec=60 StandardOutput=syslog StandardError=syslog SyslogIdentifier=cf-gortr [Install] WantedBy=multi-user.target EOF - Перезагрузка systemd для обнаружения новых сервисов:
# Reload systemctl daemon sudo systemctl daemon-reload - Генерация пары ключей для OctoRPKI 7:
# Generate keypair for OctoRPKI sudo mkdir -p /opt/cfrpki/keys/ sudo openssl ecparam -genkey -name prime256v1 -noout -outform pem > /opt/cfrpki/keys/private.pem sudo openssl ec -in /opt/cfrpki/keys/private.pem -pubout -outform pem > /opt/cfrpki/keys/public.pem - Установка ARIN TAL 9 (остальные Trust Anchors встроены):
# Download ARIN TAL sudo wget https://www.arin.net/resources/manage/rpki/arin-rfc7730.tal -O /usr/share/octorpki/tals/arin-rfc7730.tal - Добавление в загрузку при старте операционной системы и запуск сервисов:
# Enable services and run them sudo systemctl enable octorpki gortr sudo systemctl start octorpki gortr # Check both services are running sudo systemctl is-active octorpki gortr - Проверка работоспособности сервисов:
# Check status for both services sudo systemctl status octorpki gortr sudo ss -tulpn | egrep '8080|8323'
Настройка RPKI на Juniper MX:
В качестве примера выступает Stub AS.
- x.x.x.x - RIPE NCC RTR сервер
- y.y.y.y - Cloudflare RTR сервер
- a.a.a.a - Loopback IP на MX Router #1
- b.b.b.b - Loopback IP на MX Router #2/RR
- c.c.c.c - IP из Peering network MX Router
- d.d.d.d - IP из Peering network на Uplink Router (External AS)
- YYYY - AS номер на Uplink Router (External AS)
- Конфигурация RPKI сессий:
set routing-options validation group RPKI-SRV session x.x.x.x port 8323 set routing-options validation group RPKI-SRV session x.x.x.x local-address a.a.a.a set routing-options validation group RPKI-SRV session y.y.y.y port 8323 set routing-options validation group RPKI-SRV session y.y.y.y local-address a.a.a.a - Конфигурация apply-path для PROTECT-RE фильтра:
set policy-options prefix-list RPKI-SRV apply-path "routing-options validation group <*> session <*>" set policy-options prefix-list RPKI-LO apply-path "routing-options validation group <*> session <*> local-address <*>" - Конфигурация PROTECT-RE фильтра:
set firewall family inet filter PROTECT-RE term rpki-accept from source-prefix-list RPKI-SRV set firewall family inet filter PROTECT-RE term rpki-accept from destination-prefix-list RPKI-LO set firewall family inet filter PROTECT-RE term rpki-accept from protocol tcp set firewall family inet filter PROTECT-RE term rpki-accept then count rpki-accept set firewall family inet filter PROTECT-RE term rpki-accept then accept - Конфигурация комьюнити для validation state:
set policy-options community origin-validation-state-invalid members 0x4300:0.0.0.0:2 set policy-options community origin-validation-state-unknown members 0x4300:0.0.0.0:1 set policy-options community origin-validation-state-valid members 0x4300:0.0.0.0:0 - Конфигурация политик импорта для EBGP соседей:
Примечание: Используйте одинаковые значения local-preference для valid и unknown маршрутов при первичной имплементации RPKI.
set policy-options policy-statement ACCEPT-FV-RPKI term valid from protocol bgp set policy-options policy-statement ACCEPT-FV-RPKI term valid from validation-database valid set policy-options policy-statement ACCEPT-FV-RPKI term valid from route-filter 0.0.0.0/0 upto /24 set policy-options policy-statement ACCEPT-FV-RPKI term valid then local-preference 110 set policy-options policy-statement ACCEPT-FV-RPKI term valid then validation-state valid set policy-options policy-statement ACCEPT-FV-RPKI term valid then community add origin-validation-state-valid set policy-options policy-statement ACCEPT-FV-RPKI term valid then accept set policy-options policy-statement ACCEPT-FV-RPKI term invalid from protocol bgp set policy-options policy-statement ACCEPT-FV-RPKI term invalid from validation-database invalid set policy-options policy-statement ACCEPT-FV-RPKI term invalid then validation-state invalid set policy-options policy-statement ACCEPT-FV-RPKI term invalid then community add origin-validation-state-invalid set policy-options policy-statement ACCEPT-FV-RPKI term invalid then reject set policy-options policy-statement ACCEPT-FV-RPKI term unknown from protocol bgp set policy-options policy-statement ACCEPT-FV-RPKI term unknown from route-filter 0.0.0.0/0 upto /24 set policy-options policy-statement ACCEPT-FV-RPKI term unknown then local-preference 100 set policy-options policy-statement ACCEPT-FV-RPKI term unknown then validation-state unknown set policy-options policy-statement ACCEPT-FV-RPKI term unknown then community add origin-validation-state-unknown set policy-options policy-statement ACCEPT-FV-RPKI term unknown then accept - Конфигурация политик импорта для IBGP соседей:
set policy-options policy-statement ACCEPT-RPKI-IBGP term valid from community origin-validation-state-valid set policy-options policy-statement ACCEPT-RPKI-IBGP term valid then validation-state valid set policy-options policy-statement ACCEPT-RPKI-IBGP term valid then local-preference 110 set policy-options policy-statement ACCEPT-RPKI-IBGP term invalid from community origin-validation-state-invalid set policy-options policy-statement ACCEPT-RPKI-IBGP term invalid then validation-state invalid set policy-options policy-statement ACCEPT-RPKI-IBGP term unknown from community origin-validation-state-unknown set policy-options policy-statement ACCEPT-RPKI-IBGP term unknown then validation-state unknown set policy-options policy-statement ACCEPT-RPKI-IBGP term unknown then local-preference 100 - Конфигурация политик экспорта для IBGP соседей:
set policy-options policy-statement ACCEPT-FV-IBGP term FROM_INTERNET from protocol bgp set policy-options policy-statement ACCEPT-FV-IBGP term FROM_INTERNET then next-hop self set policy-options policy-statement ACCEPT-FV-IBGP term FROM_INTERNET then accept - Конфигурация IBGP соседа/RR:
set protocols bgp group IBGP-RTR type internal set protocols bgp group IBGP-RTR local-address a.a.a.a set protocols bgp group IBGP-RTR import ACCEPT-RPKI-IBGP set protocols bgp group IBGP-RTR export ACCEPT-FV-IBGP set protocols bgp group IBGP-RTR neighbor b.b.b.b - Конфигурация EBGP соседа (uplink):
set protocols bgp group EBGP_UPLINK_1 type external set protocols bgp group EBGP_UPLINK_1 local-address c.c.c.c set protocols bgp group EBGP_UPLINK_1 hold-time 360 set protocols bgp group EBGP_UPLINK_1 keep none set protocols bgp group EBGP_UPLINK_1 log-updown set protocols bgp group EBGP_UPLINK_1 import REJECT-BOGON-ASNS set protocols bgp group EBGP_UPLINK_1 import REJECT-BOGONS set protocols bgp group EBGP_UPLINK_1 import REJECT-LOCAL-AS set protocols bgp group EBGP_UPLINK_1 import REJECT-LOCAL set protocols bgp group EBGP_UPLINK_1 import ACCEPT-FV-RPKI set protocols bgp group EBGP_UPLINK_1 import NONE set protocols bgp group EBGP_UPLINK_1 export ACCEPT_EXTERNAL set protocols bgp group EBGP_UPLINK_1 export NONE set protocols bgp group EBGP_UPLINK_1 remove-private set protocols bgp group EBGP_UPLINK_1 peer-as YYYY set protocols bgp group EBGP_UPLINK_1 graceful-restart set protocols bgp group EBGP_UPLINK_1 neighbor d.d.d.d - Проверка конфигурации:
show validation session detail show validation database show validation statistics show route 1.0.0.0/24
Ссылки
1. What is RPKI? ↩
2. RPKI validator ↩
3. RPKI-to-Router protocol server ↩
4. RIPE Network Coordination Centre ↩
5. Cloudflare ↩
6. Red Hat Enterprise Linux ↩
7. OctoRPKI standalone RPKI validator ↩
8. GoRTR RPKI to Router protocol implementation ↩
9. ARIN’s Trust Anchor Locator ↩
10. The Cloudflare Blog - RPKI
11. RPKI Documentation
12. Day One BGP Secure Routing